Automatically delete inactive guest accounts
The management of guest accounts in Entra ID is an important aspect of an organization’s security and compliance policies. Inactive guest accounts create a potential security risk, as they could be misused by unauthorized users. To minimize these risks, it is important to regularly check inactive guest accounts and delete them if necessary.
Azure Automation Runbooks provide an automated resolution of inactive guest accounts to accomplish this task efficiently and reliably. In this guide, we will set up an Azure Automation Runbook that automatically deletes inactive guest accounts after 90 days of inactivity.
Index
Advantages to automatically delete inactive guest accounts
Increased security: Deleting inactive accounts reduces the attack surface for potential security threats.
Improved directory management: A tidy directory makes management easier and reduces administrative effort.
Cost savings: Avoidance of unnecessary license costs and optimization of resource usage.
Azure Automation Runbooks as a solution
Azure Automation Runbooks enable the automation of administrative tasks in Azure. They provide a robust platform to efficiently automate recurring tasks, such as monitoring and deleting inactive guest accounts. Runbooks can be used to create complex workflows that are executed regularly to ensure policies are enforced.
Instructions for creating an Azure Automation Runbook
Create an Azure Automation account
1. log in to the Azure portal at https://portal.azure.com.
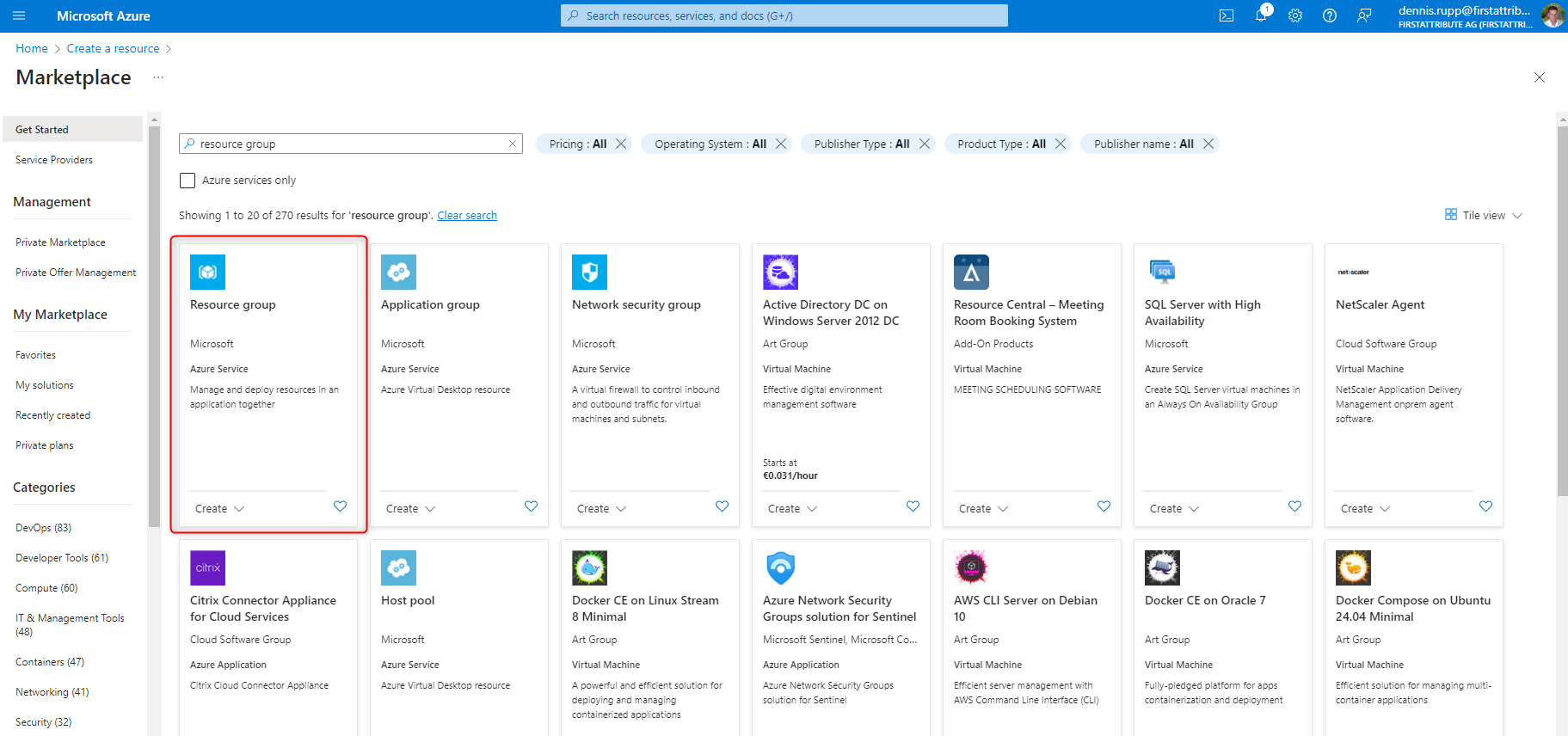
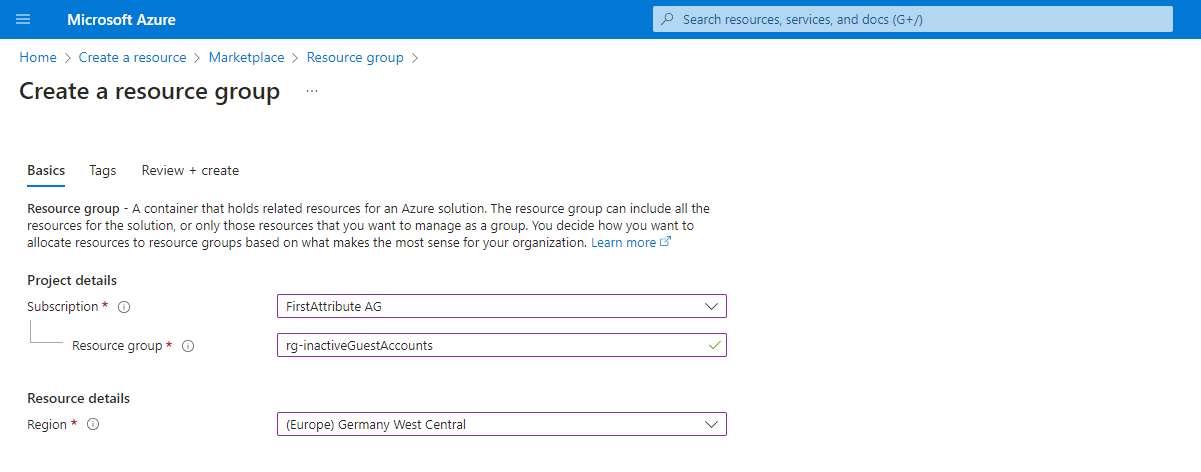
2. create a new resource group for the services via “Create resource”.
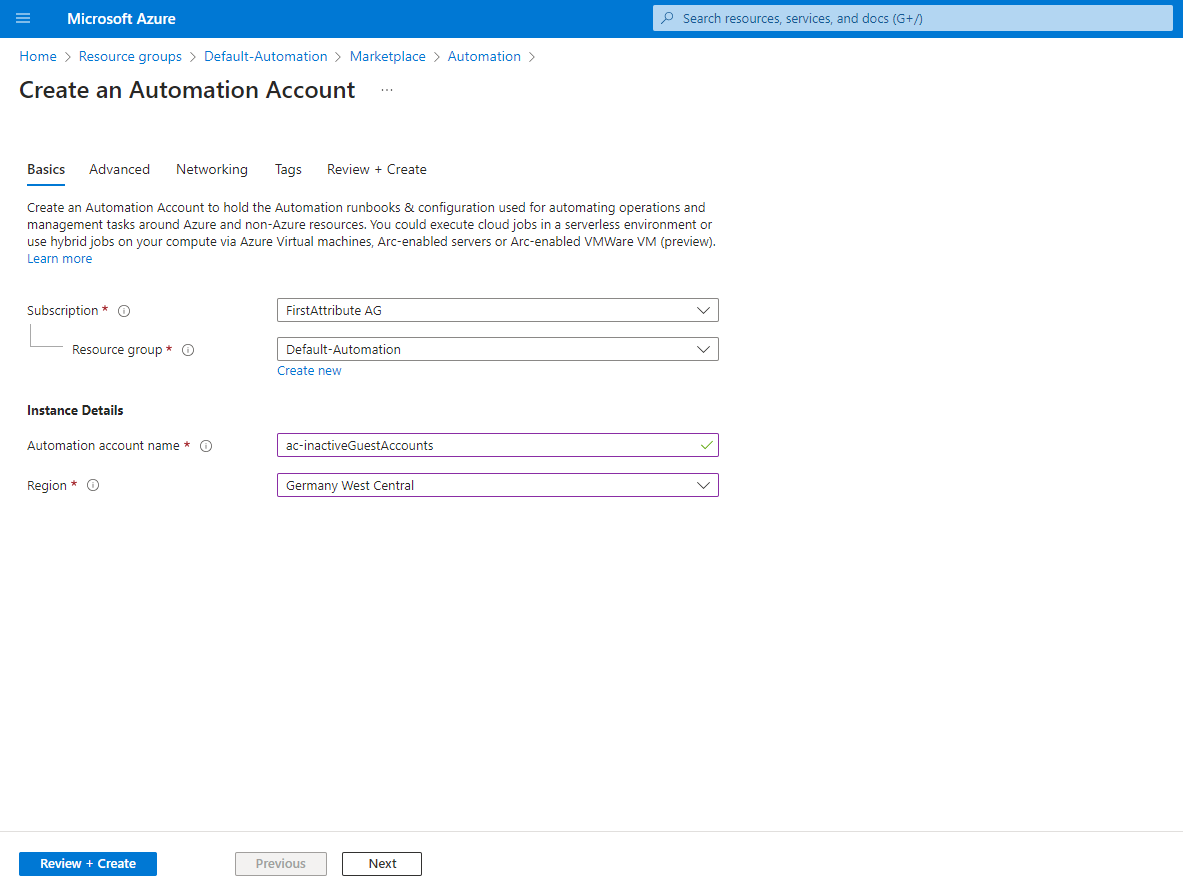
3. in the next step, we create an Automation account that is to execute our PowerShell script. To do this, we go back to “Create resource” and search for “Automation account”
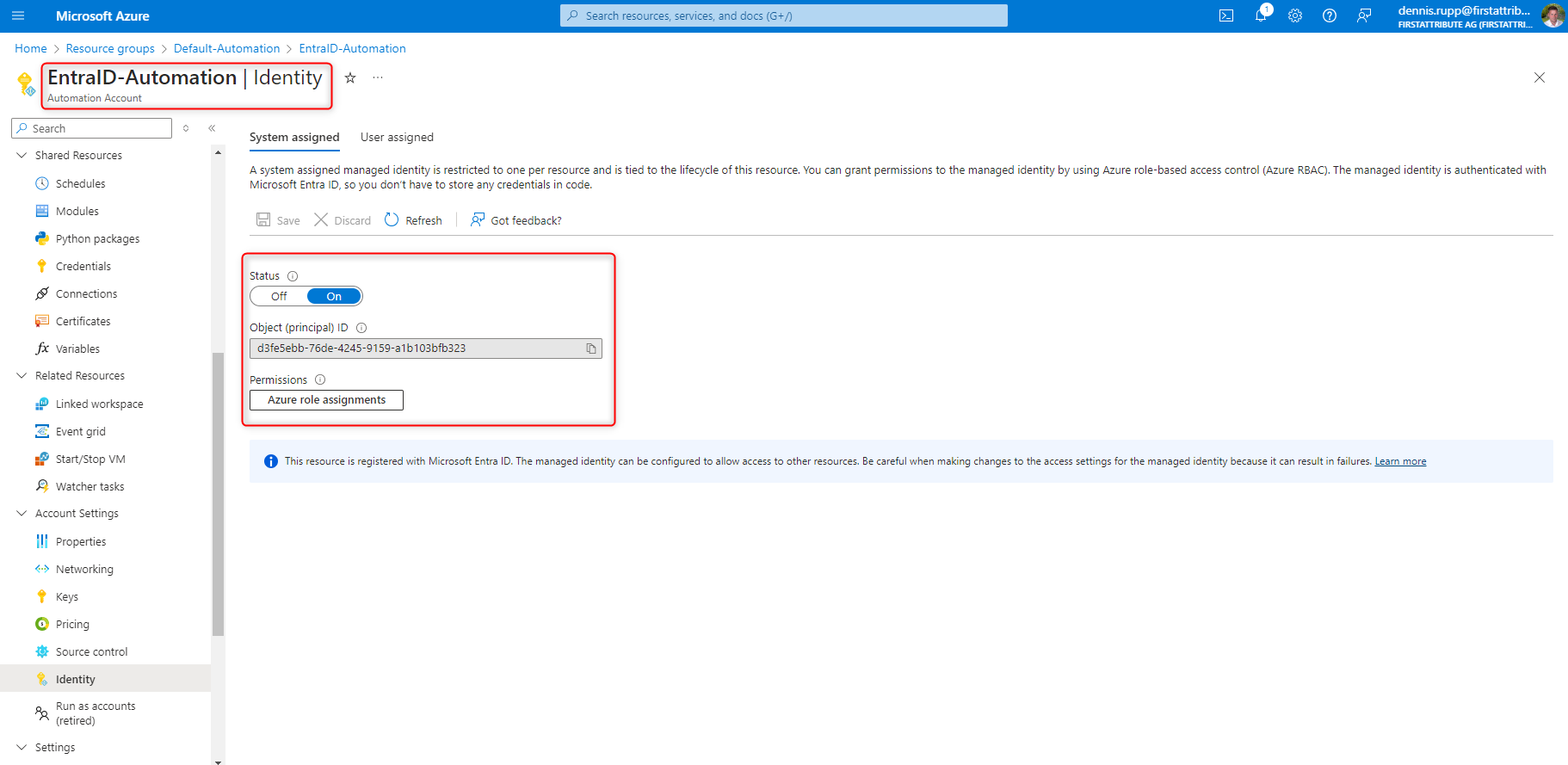
4. make sure that the “System-assigned managed identity” option was enabled when the automation account was created. Note: I strongly recommend using this option instead of the soon-to-be phased out “Run as account” option.
Creating a runbook
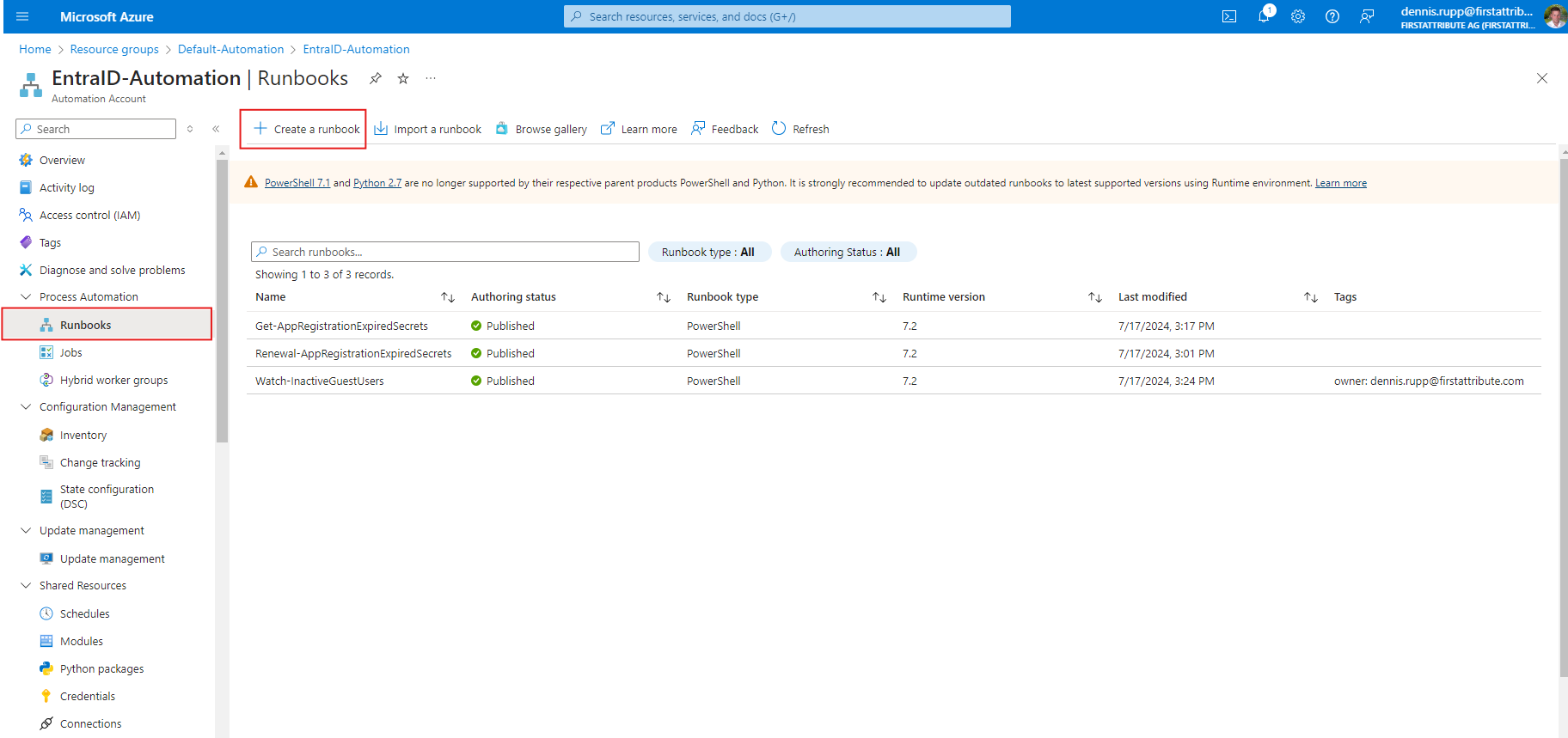
1. Let’s access the newly created automation account to initiate the creation of a new runbook.
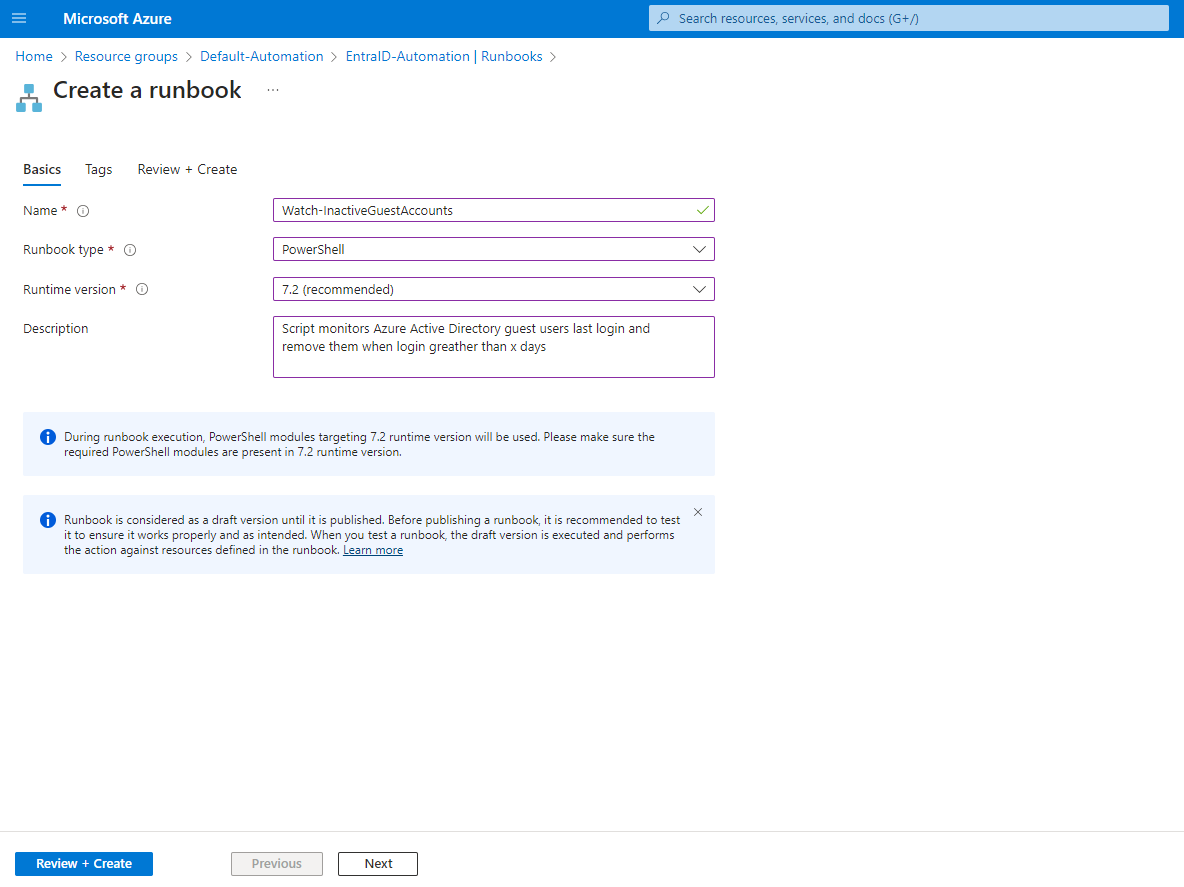
2. once we have created our runbook, insert the code below with the script to identify and delete inactive guest accounts.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 |
# Author: Max Mueller(max.mueller@firstattribute.com) # Description: Script monitors Azure Active Directory guest users last login and remove them # when login greather than x days # Version: 1.0 # Created on: 18.12.2023 # Last Change: 18.12.2023 # Changed by: Max Mueller # =========================================================================================== # Change History: # # Release: | Date: | Author: | Changes: # -----------+------------+---------------+------------------------------------------------- # 1.0 | 18.12.2023 | M. Mueller| Creation $inactiveDays = 90 $inactiveDate = (Get-Date).AddDays(-$inactiveDays) $body = "{0} has been inactive for over $($inactiveDays) days. {0} will be remove now, last logon on: {1}" $bodyNoLogin = "{0} has no login at now." Write-Output ("[info] Starting watch inactive entraID guest users...") Connect-MgGraph -Identity -NoWelcome $guestsEntraID = Get-MgUser -ConsistencyLevel eventual -Count userCount -Filter "UserType eq 'Guest'" -Property Id, DisplayName, UserPrincipalName, UserType, SignInActivity -top 10000 Write-Output ("[info] " + ($guestsEntraID.Count).ToString() + " active users found in AD.") foreach($guestEntraID in $guestsEntraID) { Write-Debug ("[debug] Checking " + $guestEntraID.UserPrincipalName + " last login date...") try { if ($null -eq $guestEntraID.SignInActivity.LastSignInDateTime) { Write-Warning -Message ("[warn] " + $bodyNoLogin -f $guestEntraID.DisplayName, $guestEntraID.SignInActivity.LastSignInDateTime) continue } if ($guestEntraID.SignInActivity.LastSignInDateTime -lt $inactiveDate){ Write-Output ("[info] " + $body -f $guestEntraID.DisplayName, $guestEntraID.SignInActivity.LastSignInDateTime) Remove-MgUser -UserId $guestEntraID.Id } } catch { Write-Error -Message ("[error] Error at remove entraID guest $($guestEntraID.DisplayName), message: $($_.Exception.Message)") } } |
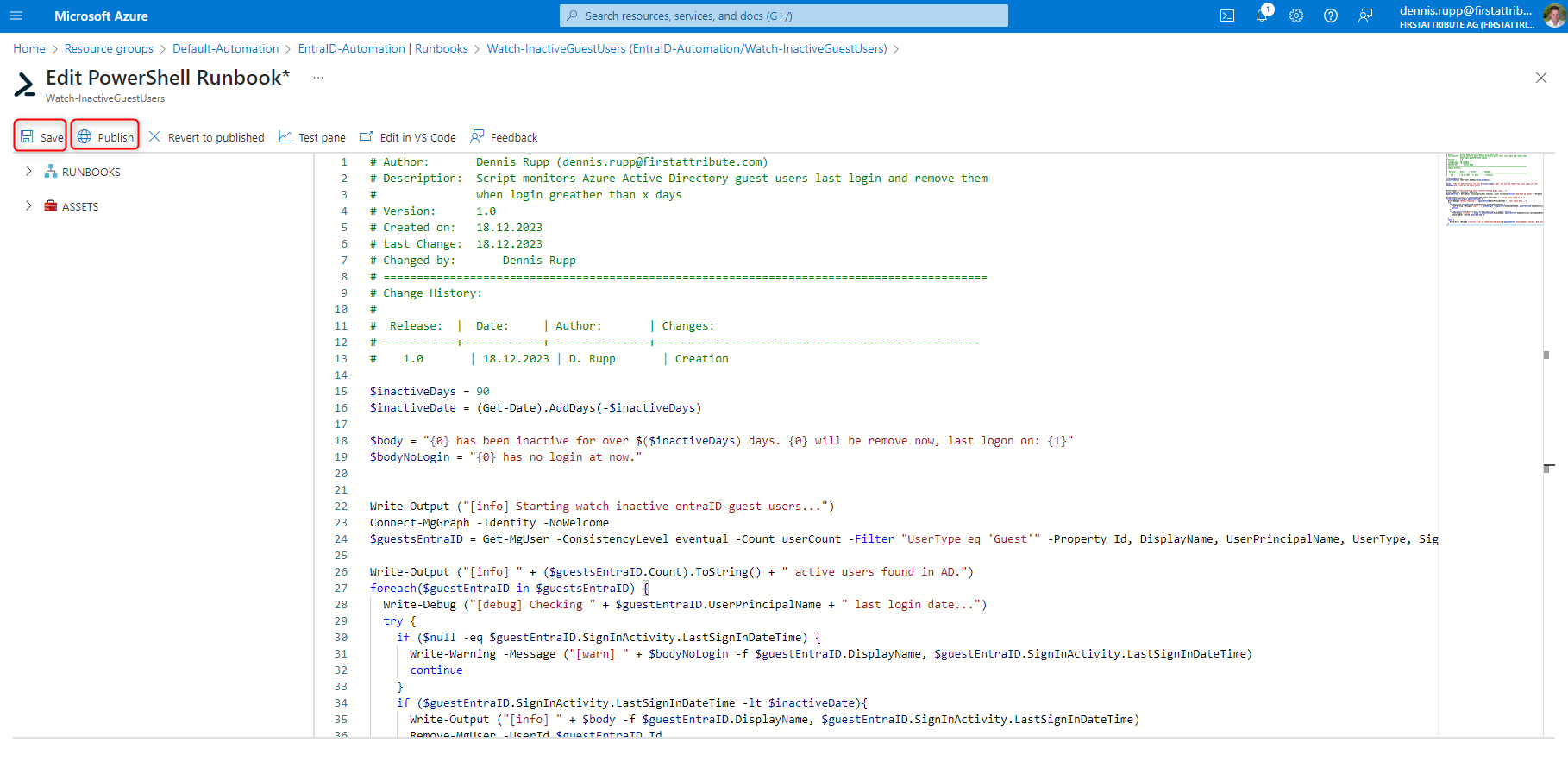
3. once the code has been inserted, click on “Save” and then on “Publish”.
Assign authorizations
The managed identity requires rights in order to be able to communicate with the Microsoft Graph API. There is no GUI for this and the commands must be executed with PowerShell.
In the PowerShell snippet, the variables $TenantID, $DisplayNameOfMSI and $PermissionName must be supplemented with the current values in order to then be able to add the authorizations for AuditLog.Read.All and User.ReadWrite.All.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
$TenantID="<your tenant id>" $GraphAppId = "00000003-0000-0000-c000-000000000000" $DisplayNameOfMSI="<name of managed identity>" $PermissionName = "User.ReadWrite.All" Install-Module AzureAD Connect-AzureAD -TenantId $TenantID $MSI = (Get-AzureADServicePrincipal -Filter "displayName eq '$DisplayNameOfMSI'") $GraphServicePrincipal = Get-AzureADServicePrincipal -Filter "appId eq '$GraphAppId'" $AppRole = $GraphServicePrincipal.AppRoles | Where-Object {$_.Value -eq $PermissionName -and $_.AllowedMemberTypes -contains "Application"} New-AzureAdServiceAppRoleAssignment -ObjectId $MSI.ObjectId -PrincipalId $MSI.ObjectId -ResourceId $GraphServicePrincipal.ObjectId -Id $AppRole.Id |
Install additional PowerShell modules
In order for the modules used to be loaded, we need to import them into our Automation account.
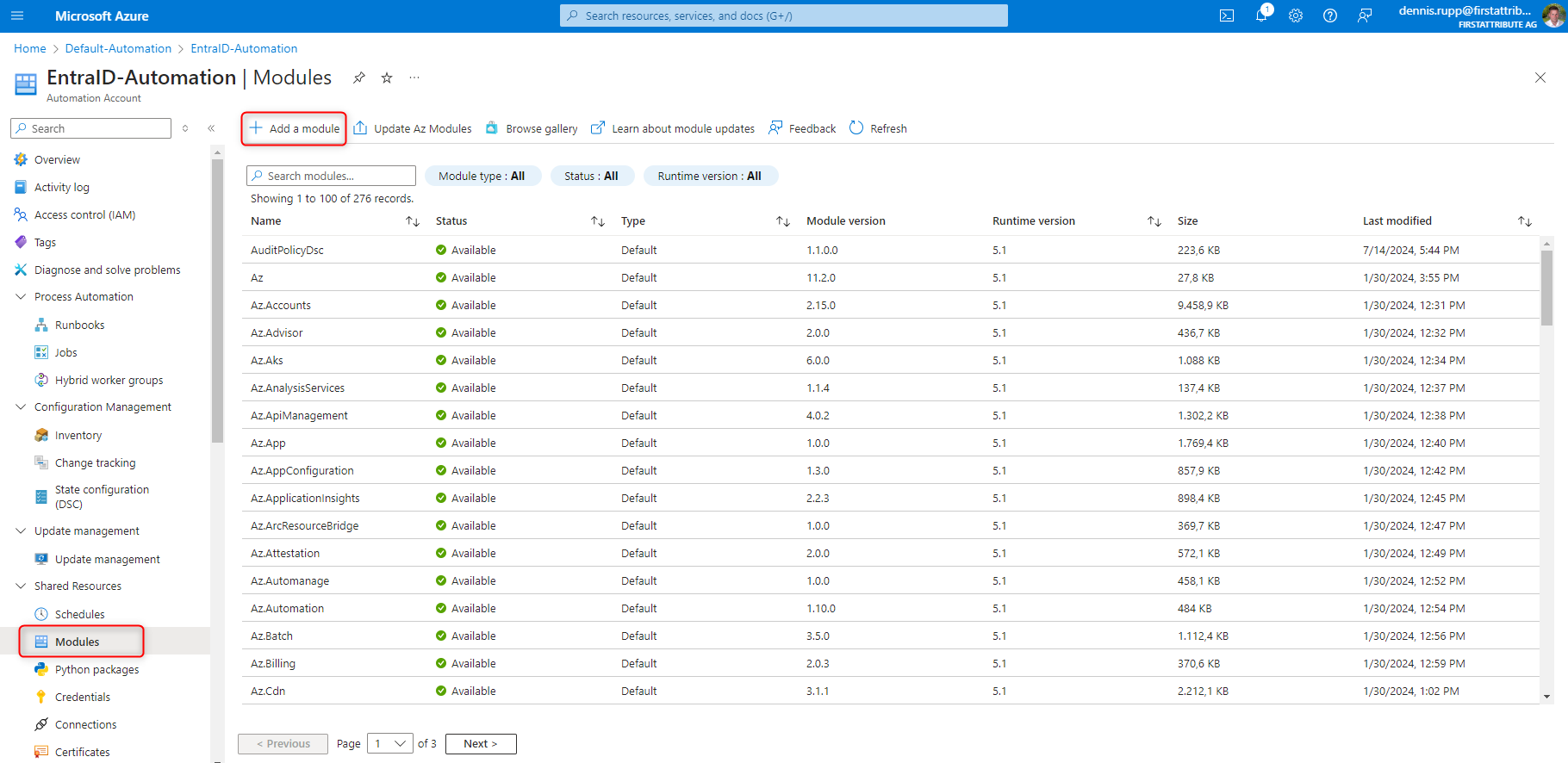
- Navigate to the automation account and click on “Add a module” under the “Modules” menu item.
Here we select the following modules from the PS Gallery:
- Microsoft.Graph.Authentication
- Microsoft.Graph.Users
 Set up and test planned task
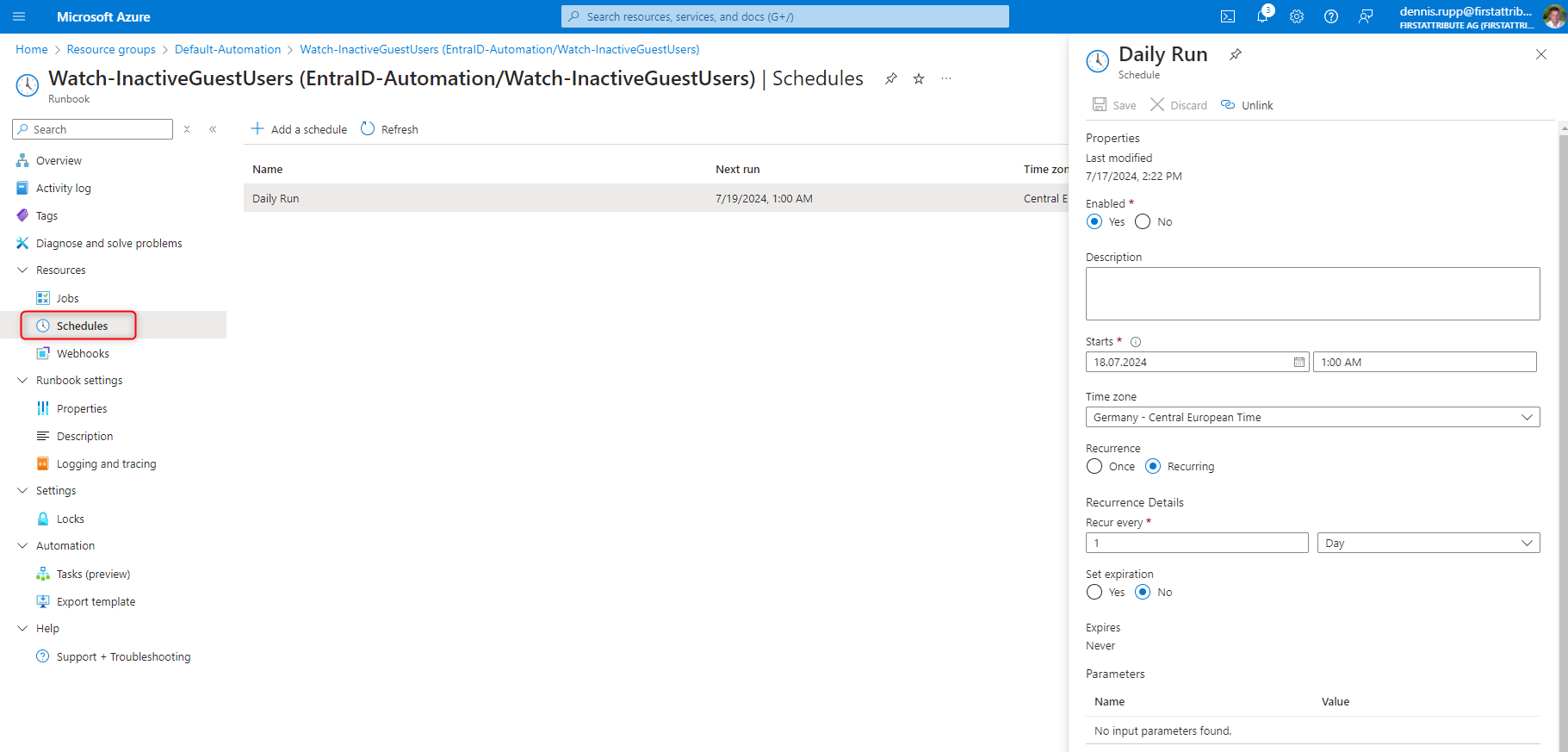
Set up and test planned task
Once all the steps have been completed, we need to set a timer and test the runbook for the automatic deletion of inactive guest accounts.
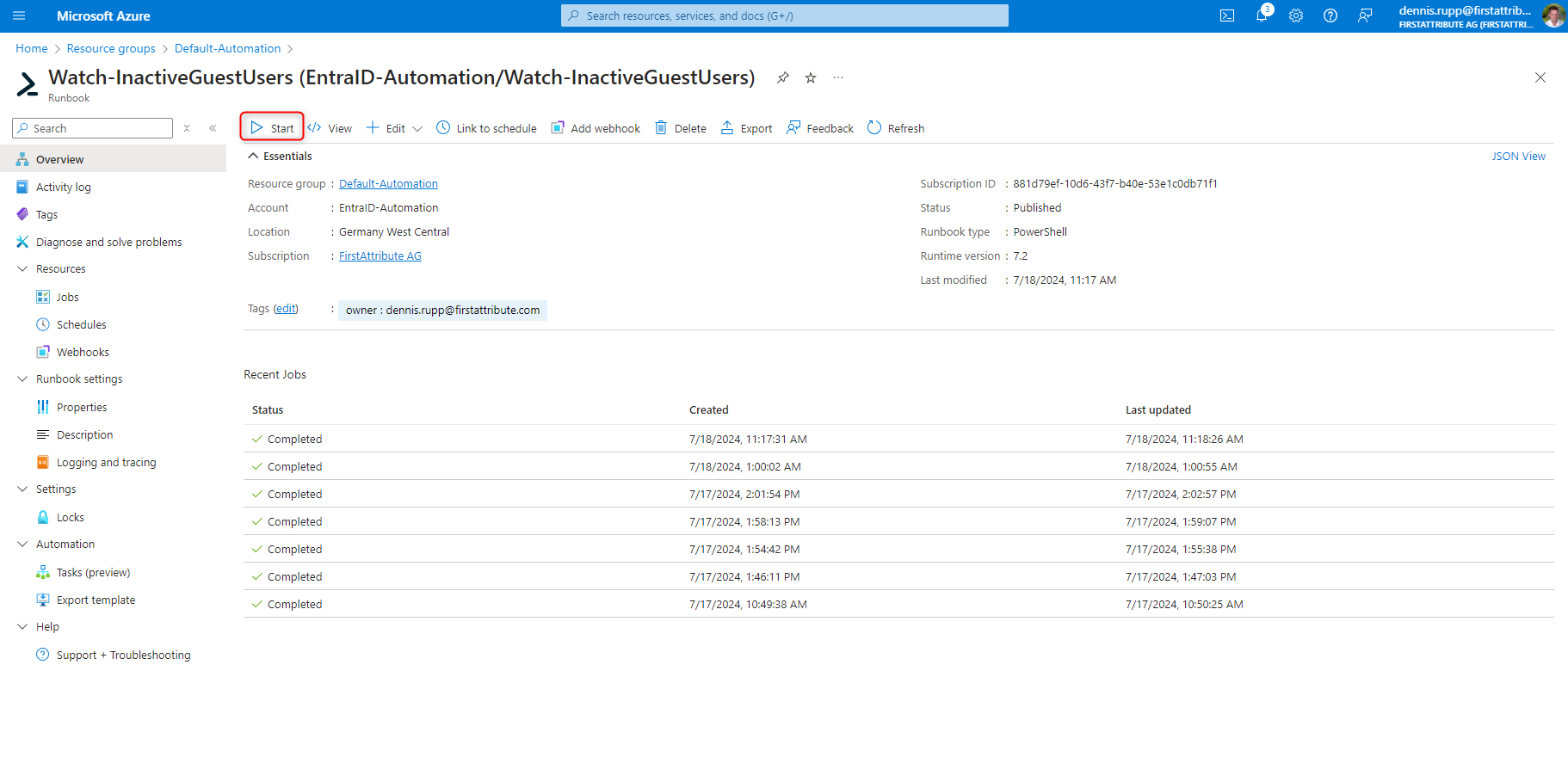
To do this, we select our runbook and create a new timer. In our case, we run the script daily.
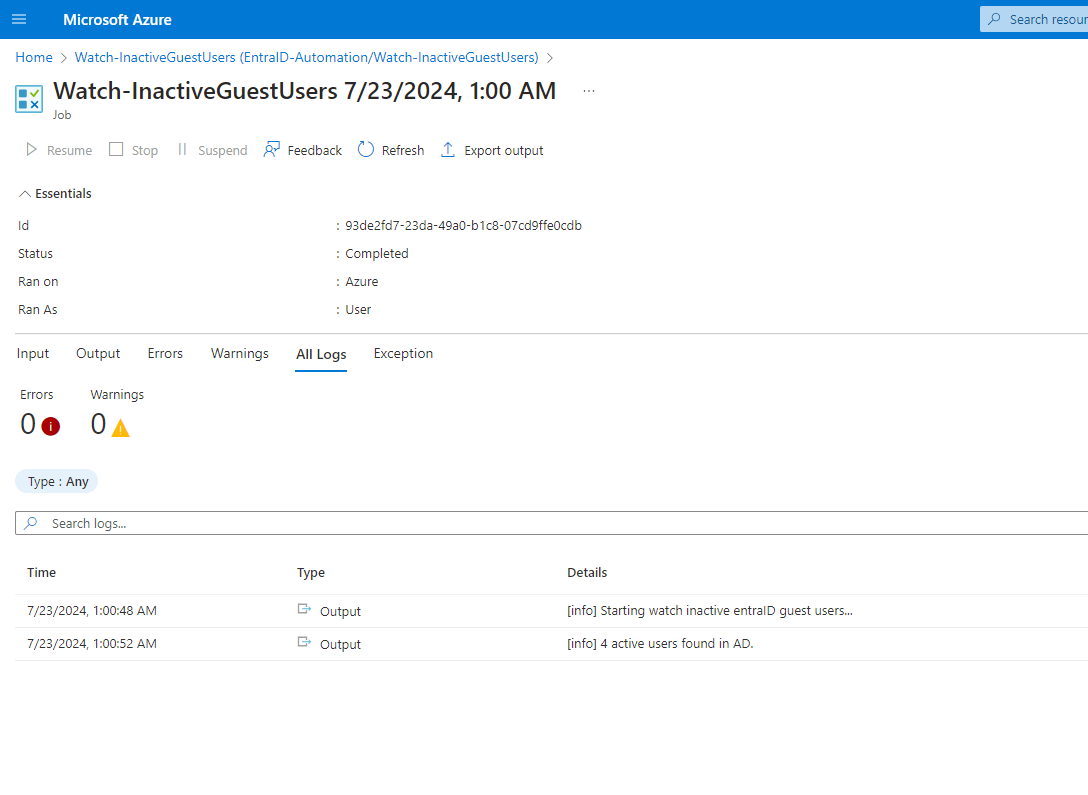
After we have set the timer, we start the runbook in the overview page, where we can also view the log entries that our script has created.
Fazit
Automatically deleting inactive guest accounts using Azure Automation Runbooks ensures that our directory always remains up-to-date and secure. By regularly checking and cleaning up the directory, potential security gaps can be closed and administrative effort reduced. Azure Automation offers a flexible and scalable solution that can be seamlessly integrated into our existing workflows.
my-IAM RealIdentity for Providing All Types of Identities
Our cloud service, my-IAM RealIdentity, enables distributed identity management:
RealIdentity collects identity data from various source systems, sorts, combines, cleanses, and updates the data, and makes it available for all kinds of applications. Consequently, companies use RealIdentity as the primary source for their identity data required in external applications.
You can also reach our team by telephone at
+49 8196 998 4330.



 Set up and test planned task
Set up and test planned task