Identity Management in Multi-Tenant: Challenges and Solutions
Identity management in multi-tenant environments poses significant challenges for companies. Multi-tenant environments are increasingly shaping the IT landscape of companies with complex structures.
Organizations with multiple locations, subsidiaries, or independent business units face the challenge of managing identities from multiple isolated IT systems centrally. These systems often include individual user accounts, access policies, and resource assignments that operate independently.
However, centralized management of these identities is a crucial factor as it facilitates collaboration while adhering to security standards.
Index
What are Multi-Tenant Environments?
Multi-tenant environments are IT infrastructures where multiple independent tenants coexist within a shared system. Each tenant represents a logically isolated entity with its own users, access rights, data, and applications.
This architecture is often used in companies with multiple locations, departments, or subsidiaries. It serves to separate different organizational units technically while enabling efficient use of shared resources.
In a multi-tenant environment, each department or region of a company can manage its specific IT applications and data. On the other hand, central functions such as cloud services, storage, or security policies are provided jointly for all tenants. This separation enables flexible management without compromising the security or autonomy of individual units.
Multi-tenant environments are particularly beneficial for organizations experiencing dynamic growth, such as through acquisitions. At the same time, they allow compliance with varying regional compliance and security requirements. They offer the necessary flexibility and scalability to efficiently operate complex IT landscapes.
Challenges in Multi-Tenant Environments
Multi-tenant environments come with both technical and organizational challenges that companies must address.
One of the major difficulties is ensuring tenant isolation. Each unit within a multi-tenant environment requires protection from unauthorized access by other tenants, especially concerning sensitive data or critical applications. At the same time, it may be necessary to share certain resources or platforms across tenants, which demands precise control of access rights.
Another challenge lies in maintaining consistency in identity data. Different source systems, such as local directories, Active Directory environments, and cloud-based solutions, can lead to conflicts like duplicate user accounts or contradictory permissions. These inconsistencies complicate synchronization and can create security gaps, making an efficient multi-tenant identity management strategy essential. Granular rights management also often reaches its limits, as IAM systems may not always accommodate the specific requirements of individual tenants.
Additionally, varying compliance requirements and legal standards present significant challenges. In global multi-tenant environments, regional and national regulations must be adhered to without compromising the efficiency of central management.
Companies are tasked with establishing flexible yet standardized processes to meet both local and global requirements. Striking this balance necessitates well-thought-out strategies and the use of specialized technologies and tailored solutions.
👉 In multi-tenant identity management, not only internal identities must be managed but also external identities that need to be accessed by various tenants. For more information on using and managing external identities, check out our article “Utilizing and Managing External Identities.“
Scenarios for Using Multi-Tenant Environments
A typical example of multi-tenant environments is a company that regularly acquires other organizations. Each acquired unit brings its own IT systems and user directories, often based on different technologies, such as Microsoft Entra ID, on-premises Active Directory instances, or proprietary solutions.
Without a centralized IAM solution, problems arise: users cannot seamlessly access shared resources, and the IT department must manage permissions manually. At the same time, the existing policies of the acquired unit must be respected, as they may be tied to local legal requirements or industry-specific standards. This complexity makes IAM in multi-tenant environments one of the key pillars of IT security and efficiency.
Another scenario arises in organizations that structure their IT environment globally. Regions or countries often operate their own tenants to meet local compliance requirements, such as data protection laws or specific security standards. At the same time, global departments, such as IT or finance, need access to company-wide resources without compromising the autonomy of regional units. This requires a flexible yet consistent administration approach that is centrally managed but locally adaptable. Such requirements can only be met through a well-thought-out multi-tenant strategy that tackles both organizational and technical challenges.
What is Identity Management in Multi-Tenant Environments?
Identity management in multi-tenant environments involves the management of user identities and access rights in complex scenarios with multiple isolated tenants. Each tenant acts as an independent entity with its own policies, users, and resources. This isolation primarily serves security purposes, ensuring that no unauthorized access occurs between tenants. However, it also presents challenges when centralized control is required, such as for company-wide security policies or managing shared platforms like ERP or CRM systems.
A multi-tenant identity management system must be capable of consolidating identities from different sources and managing them centrally. The goal is a unified control of access rights and security standards without violating the specific needs of individual tenants. A common example is integrating hybrid IT environments, where on-premises directories like Active Directory are combined with cloud-based platforms. Here, user accounts from both worlds must be synchronized to ensure all employees have access to both local resources and cloud services. This requires consistent management that avoids duplicate accounts and conflicting permissions.
Another example is implementing centralized security policies. In a multi-tenant environment, it may be necessary to enforce global measures such as multi-factor authentication or access restrictions to sensitive data. However, these measures must be designed in a way that does not hinder the local requirements of individual tenants.
Best Practices for Identity Management in Multi-Tenant Environments
Introduction of a Central IAM Platform
Managing multi-tenant environments requires a clear strategy and the use of modern technologies. In particular, the introduction of a central IAM platform is crucial for consolidating identities from various sources. This platform must be able to automatically synchronize user accounts and implement changes in real time. This not only reduces administrative overhead but also ensures that all data remains consistent and up-to-date. In large organizations that frequently add new tenants, this automation is indispensable to avoid manual errors and enhance efficiency.
Granular Access Control
A central aspect of managing multiple tenants is granular control over access rights. Companies can define global security policies, such as implementing Zero-Trust models, centrally, while also making local adjustments. For example, access can be restricted to specific geographical locations or devices. While the central IT department monitors security guidelines, local teams adjust settings to meet the specific requirements of their region or department.
Dynamic Role Models
The introduction of dynamic role models is also a key factor in this area. These models allow user accounts to be automatically assigned the appropriate permissions based on their role, department, or function. An example is the automatic assignment of rights for new employees. Once an employee is registered in a particular department, they automatically gain access to relevant resources without the need for manual intervention. This significantly reduces administrative effort and ensures that permissions always meet current requirements.
Limitations and Challenges in Multi-Tenant Environments
Consistency of Identity Data
Despite modern technologies, there are still technical and organizational limitations when managing multi-tenant environments. In particular, the consistency of identity data remains one of the biggest challenges. Different source systems and technologies often lead to inconsistencies, such as duplicate user accounts or conflicting permissions. Such conflicts complicate synchronization and increase the risk of security gaps. Without robust mechanisms for data validation and cleansing, management quickly becomes inefficient and error-prone.
Tenant Isolation
Another challenge is tenant isolation. While multi-tenant systems allow centralized control, it is crucial to ensure that the data and access rights of tenants remain strictly separated. However, it is often necessary to enable collaboration between tenants, such as sharing platforms or resources. Achieving the balance between isolation and collaboration is technically demanding and requires flexible and clearly defined policies.
Granular Access Management Capabilities
The granular capabilities of access management also often reach their limits. In many IAM systems, it is difficult to tailor permissions precisely to the needs of individual tenants. This results either in unnecessarily broad rights, which pose a security risk, or in restrictions that hinder productivity. A well-thought-out access management system that takes both central and local requirements into account is essential.
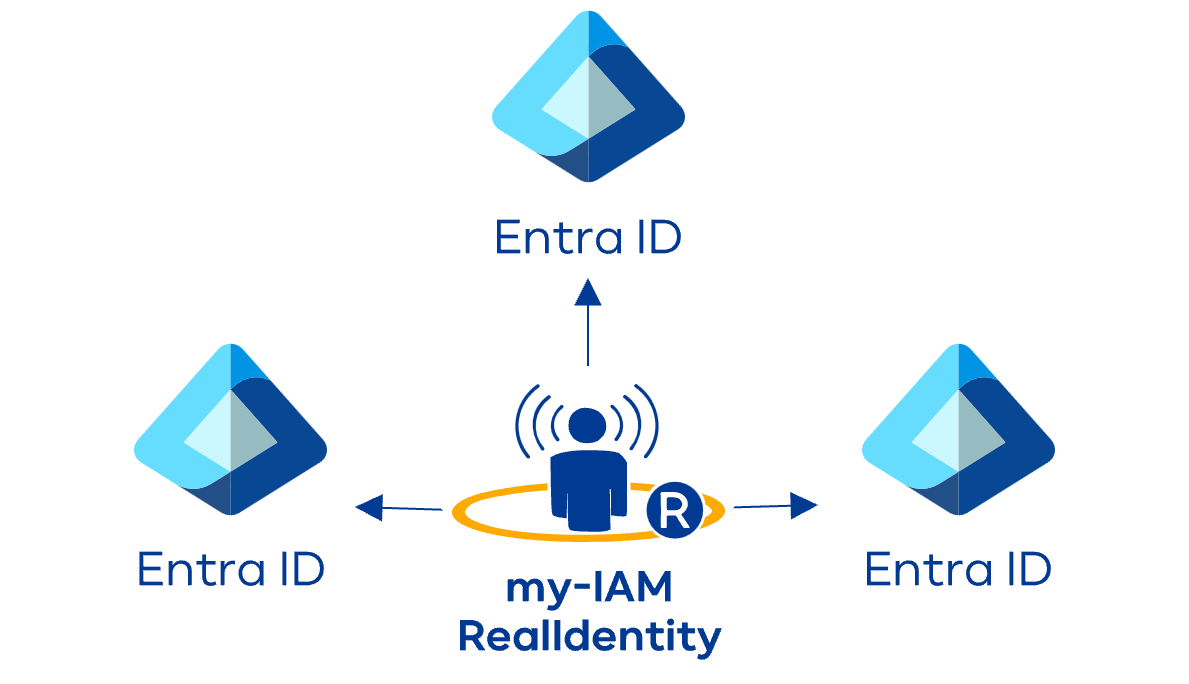
Distributed Identity Management with the my-IAM Platform
To effectively address the challenges of Identity and Access Management (IAM) in multi-tenant environments, it is recommended to use specialized solutions like the my-IAM platform. This platform integrates identities from various source systems and makes them available to applications in real time.
A central component of the my-IAM platform is RealIdentity, a cloud service that consolidates enterprise identities from different sources. This Software-as-a-Service (SaaS) solution unites identities from employees, customers, partners, and suppliers and makes them available for target applications in real time. This enables seamless integration into existing systems and ensures fast, reliable data processing and synchronization for applications of all types.
my-IAM RealIdentity kann Daten aus unterschiedlichen Tenants abrufen, abgleichen, konsistent halten und für andere Tenants oder Anwendungen bereitstellen.
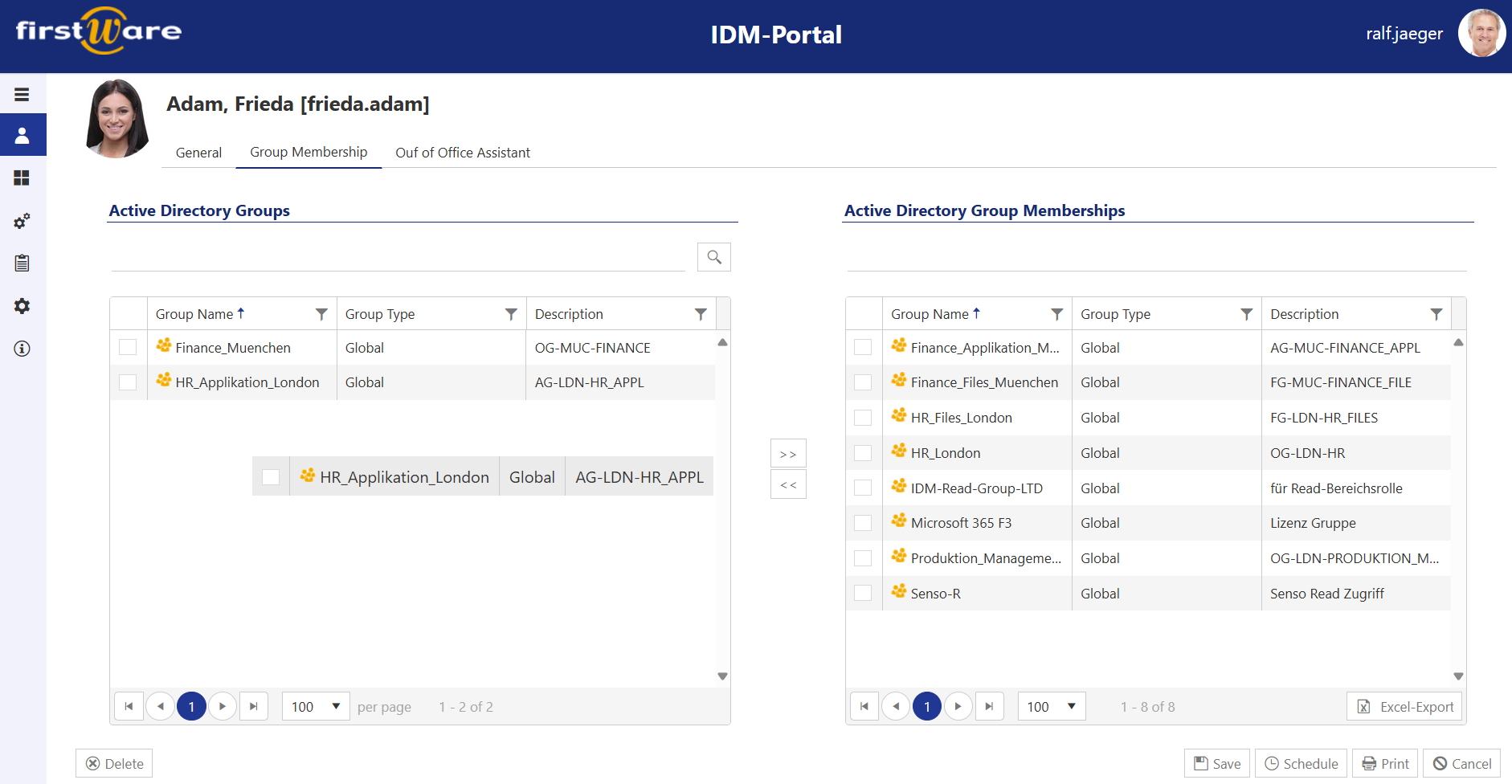
Centralized identity management in multi-tenant environments – with IDM-Portal
my-IAM RealIdentity provides consistent identity data for other applications – for example in a central IAM interface to efficiently control the management of multiple tenants. One such solution is the IDM-Portal, which enables clear and uniform user management.
Through integration with my-IAM RealIdentity, administrators can manage all identities from different tenants in a central interface without having to perform a complex migration. This allows users, groups and authorizations to be managed efficiently while ensuring a uniform security and compliance strategy.
Use case: Simplified management for IT administrators
A company with several subsidiaries operates different Entra ID tenants for each business unit. Previously, IT administrators had to log into each tenant individually to manage users or adjust permissions. This was time-consuming, error-prone and difficult to scale.
With the combination of my-IAM RealIdentity and the IDM-Portal, administrators can now:
-
Centrally manage all users and groups from different tenants
-
Control authorisations uniformly across tenants
-
Ensure that identity data remains synchronised and consistent
-
Additionally optimise licensing costs by identifying duplicate or unnecessary accounts
This eliminates the need for manual administration and gives the IT department more control over the security and efficiency of identity management.
Conclusion
By using these specialised tools, companies can reduce the complexity of IAM in multi-tenant environments, increase security and improve the efficiency of their IT infrastructures. The my-IAM platform offers flexible management options and prepares identity data intelligently so that companies can optimise the use of their existing resources.
More About the my-IAM Platform